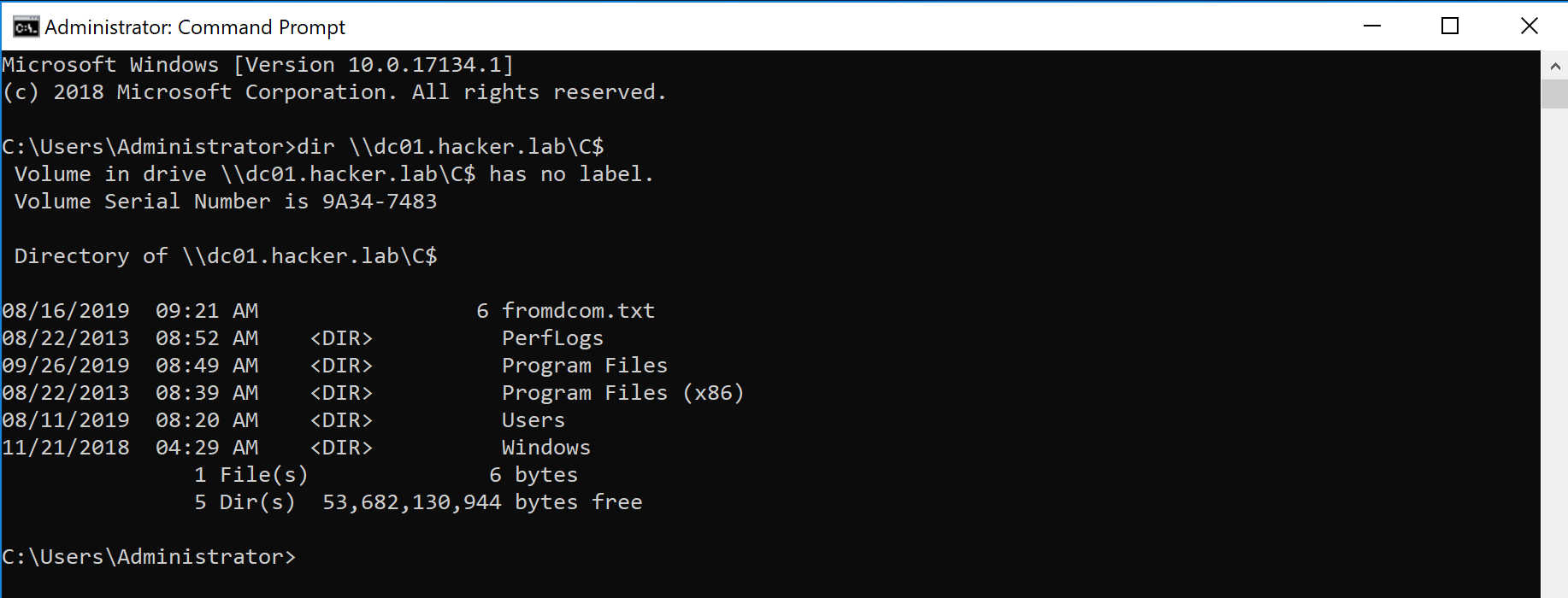
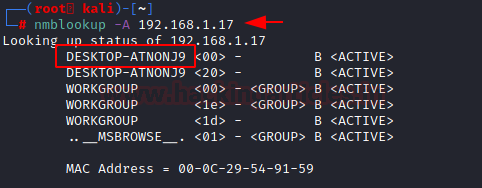
Detecting LDAP enumeration and Bloodhound's Sharphound collector using AD Decoys | by Madhukar Raina | Securonix Tech Blog | Medium

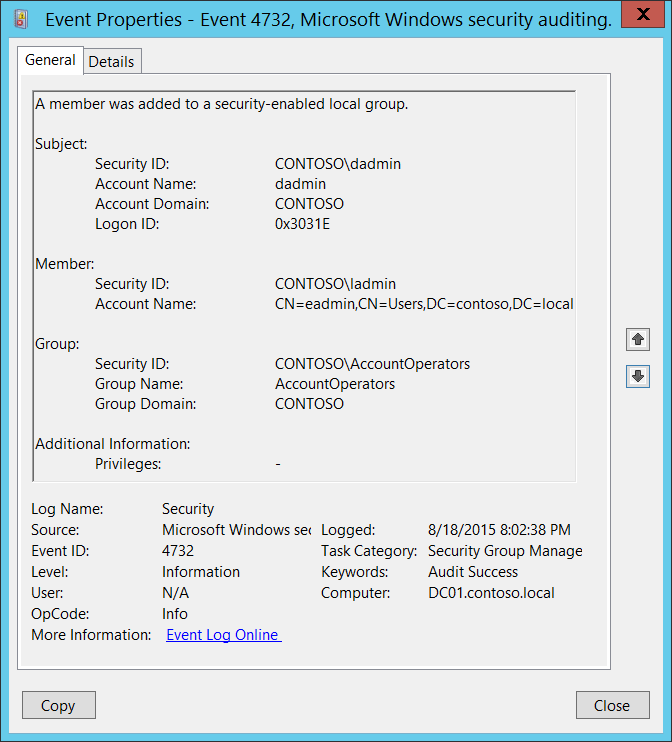
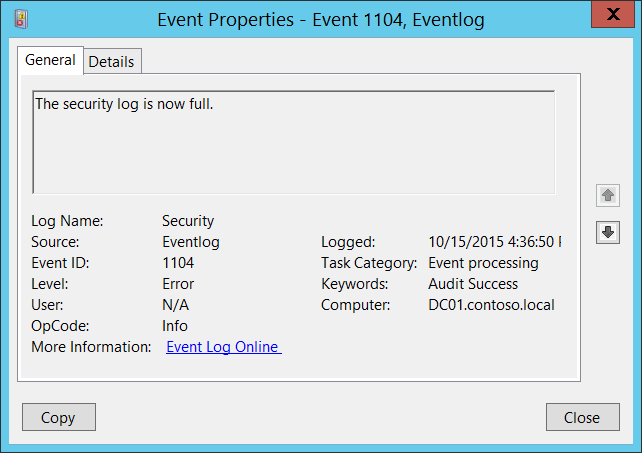
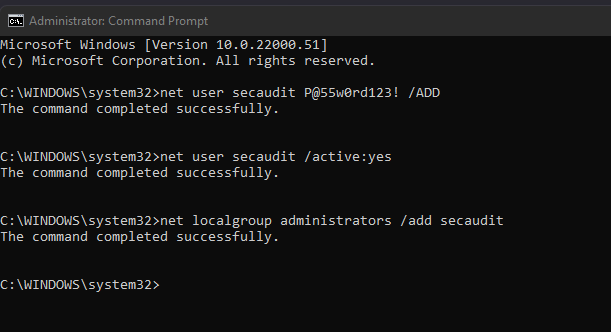
Active Directory Enumeration detected by Microsoft Security solutions | by Derk van der Woude | Medium
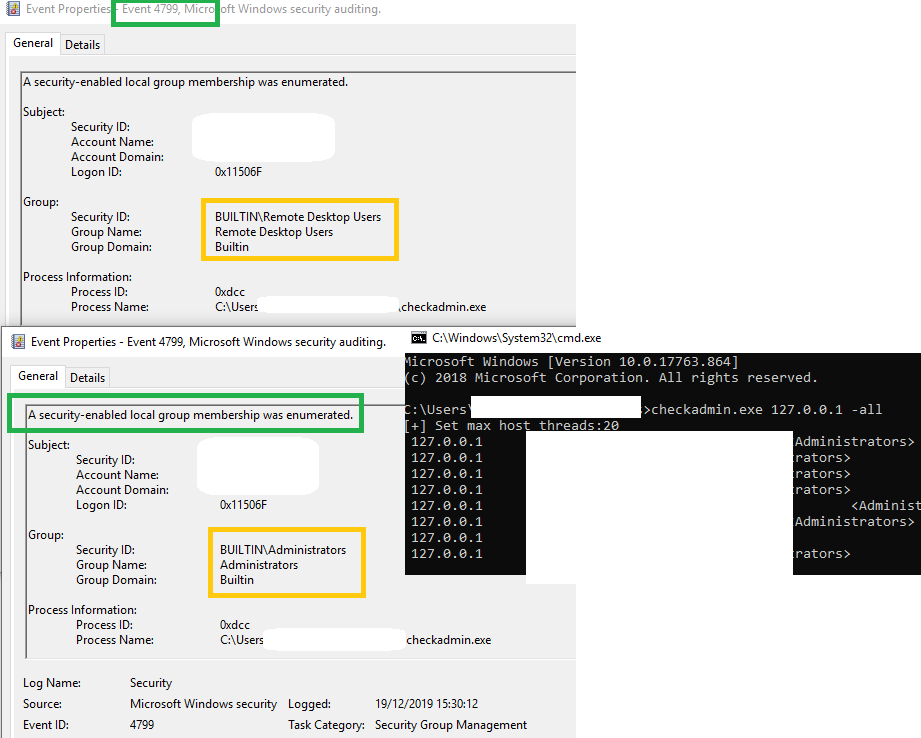
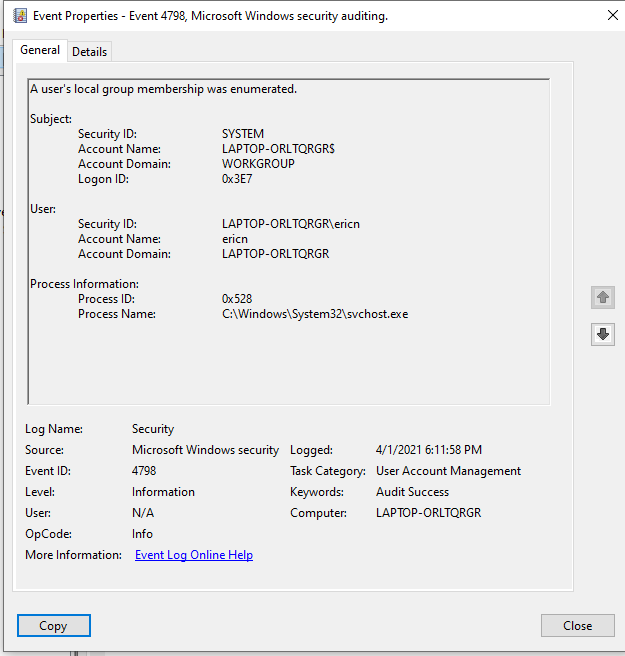
Samir on Twitter: "the cool thing about those 2 newly introducted MS security eventid 4799, 4798 is that they will capture any local group/user discovery attempts even if done via winapis, below